Server Security Breach Financial Impact Analysis
 Server Security Breach Financial Impact Analysis
Server Security Breach Financial Impact Analysis
When organizations consider cybersecurity, they often focus on technical vulnerabilities and software patches. However, the most significant impact of a server security breach extends far beyond compromised data – it creates a profound financial catastrophe that can cripple organizations for years. A server breach represents one of the most severe cyber incidents because servers house an organization’s most valuable digital assets: customer databases, intellectual property, financial records, and operational systems. This comprehensive analysis examines the multifaceted financial impact of server security breaches, breaking down both immediate and long-term costs, exploring the hidden expenses most organizations overlook, and providing a strategic framework for calculating risk and implementing cost-effective prevention measures.
A. Understanding Server Breach Severity: Beyond Basic Hacking
A server security breach occurs when unauthorized individuals gain access to an organization’s server infrastructure. Unlike endpoint compromises, server breaches threaten the entire organizational foundation.
A. Why Server Breaches Create Maximum Damage:
Servers act as central repositories for organizational data and operations. When compromised, attackers gain access to:
-
Complete customer databases with personal identifiable information (PII)
-
Financial systems and banking credentials
-
Intellectual property and trade secrets
-
Authentication systems and administrative controls
-
Operational technology and production systems
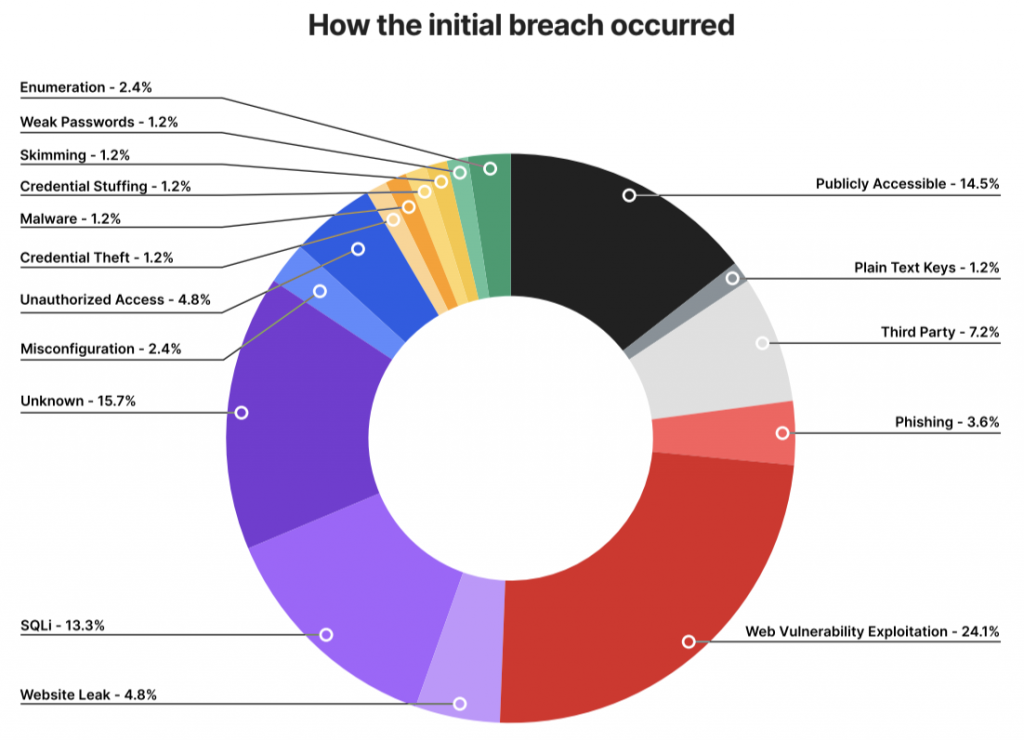
B. Common Server Breach Vectors:
A. Unpatched Vulnerabilities: Exploitation of known security flaws in server operating systems or applications.
B. Phishing and Credential Theft: Compromised administrative credentials providing direct server access.
C. Misconfigured Cloud Services: Improperly secured cloud storage buckets or database instances.
D. Third-Party Vendor Compromises: Attacks through connected vendor systems with server access.
E. Advanced Persistent Threats: Sophisticated, long-term infiltration by organized threat actors.
C. The Expanding Attack Surface:
Modern server environments have dramatically expanded the potential breach landscape:
-
Hybrid Infrastructure: Combining on-premises servers with cloud instances (AWS, Azure, Google Cloud)
-
Containerized Environments: Kubernetes clusters and Docker containers with their own security challenges
-
Legacy Systems: Older servers that cannot be patched or updated due to compatibility requirements
-
Remote Management Interfaces: Web-based control panels that provide external access points
B. Immediate Financial Impacts: The First Wave of Costs
The initial financial impact of a server breach begins within hours of detection and can overwhelm unprepared organizations.
A. Incident Response and Forensic Investigation:
Immediately following breach detection, organizations must engage specialized resources:
-
Digital Forensics Teams: $300-$500 per hour for expert analysis of breach scope and origin
-
Incident Response Retainers: $50,000+ for guaranteed response availability
-
Evidence Preservation: Costs associated with maintaining legal chain of custody for digital evidence
-
Breach Assessment: Determining exactly what data and systems were compromised
B. Business Interruption and Downtime Costs:
When critical servers go offline, business operations halt:
-
Lost Revenue: Direct sales interruption, especially for e-commerce and SaaS companies
-
Employee Productivity Loss: Staff unable to perform their primary job functions
-
Recovery Time: The period required to restore systems from backups or rebuild compromised servers
-
Contractual Penalties: Failure to meet service level agreements (SLAs) with customers
C. System Recovery and Restoration:
Returning to normal operations requires significant investment:
-
Data Restoration: From clean backups, assuming they exist and weren’t compromised
-
Server Rebuilding: Completely reinstalling operating systems and applications
-
Security Hardening: Implementing proper security controls before bringing systems back online
-
Network Segmentation: Isocating affected systems to prevent breach spread
D. Regulatory Notification Requirements:
Most jurisdictions mandate strict breach notification timelines:
-
Customer Notification: Costs of mail, email, and call center operations to inform affected individuals
-
Regulatory Reporting: Preparing and submitting detailed reports to government agencies
-
Legal Consultation: Ensuring compliance with multiple jurisdictional requirements
-
Credit Monitoring Services: Typically offered to affected individuals for 1-2 years
C. Long-Term Financial Consequences: The Hidden Cost Iceberg
While immediate costs are substantial, the long-term financial impact often proves more devastating to organizational health.
A. Regulatory Fines and Legal Penalties:
The regulatory landscape has become increasingly punitive:
-
GDPR (General Data Protection Regulation): Fines up to 4% of global annual revenue or €20 million, whichever is higher
-
HIPAA (Health Insurance Portability and Accountability Act): Penalties up to $1.5 million per violation category per year
-
CCPA (California Consumer Privacy Act): $2,500 per unintentional violation, $7,500 per intentional violation
-
Sector-Specific Regulations: Financial services, education, and government contractors face additional penalties
B. Class Action Litigation and Legal Settlements:
Data breaches frequently generate significant legal action:
-
Class Action Lawsuits: Filed on behalf of affected customers whose data was compromised
-
Individual Lawsuits: From particularly impacted individuals facing identity theft or fraud
-
Legal Defense Costs: Attorney fees, court costs, and expert witness expenses
-
Settlement Amounts: Often reaching millions of dollars even before trial
C. Reputational Damage and Customer Attrition:
The intangible cost of damaged trust has tangible financial consequences:
-
Customer Churn: Loss of existing customers who no longer trust the organization
-
Acquisition Cost Increase: Higher marketing spend required to attract new customers
-
Brand Value Erosion: Decreased company valuation and market perception
-
Competitive Advantage Loss: Customers migrating to perceived safer alternatives
D. Increased Insurance and Compliance Costs:
Post-breach financial impacts extend to ongoing operational expenses:
-
Cyber Insurance Premiums: Dramatic increases following claims, if coverage remains available
-
Third-Party Audits: Required by insurers, regulators, or business partners
-
Security Control Implementation: Costs for tools and staff previously deemed unnecessary
-
Ongoing Monitoring Services: Continuous threat detection and response capabilities
D. Quantifying the Total Cost: Industry-Specific Analysis
The financial impact varies significantly across industries based on data sensitivity and regulatory environments.
A. Healthcare Organizations:
-
Average Cost: Highest among all sectors at approximately $10.93 million per breach
-
Factors: HIPAA violations, medical identity theft, patient safety concerns, electronic health record system restoration
-
Case Example: A breached hospital system faced $3 million in immediate costs plus $8.5 million in HIPAA settlements
B. Financial Services Institutions:
-
Average Cost: $5.90 million per breach, excluding regulatory penalties
-
Factors: Banking regulator oversight, credit monitoring for millions of customers, stock value impact
-
Case Example: A regional bank spent $15 million recovering from a server breach, plus 12% customer attrition
C. Retail and E-Commerce:
-
Average Cost: $3.28 million per breach, heavily weighted toward business interruption
-
Factors: Point-of-sale system compromises, payment card reissuance, holiday season disruption
-
Case Example: A major retailer lost $25 million in holiday sales during a 3-day server outage
D. Technology and SaaS Companies:
-
Average Cost: Varies widely based on company size, but averages $4.35 million
-
Factors: Intellectual property theft, source code exposure, customer data protection obligations
-
Case Example: A SaaS provider lost 40% of its valuation following breach disclosure
E. The Ransomware Factor: Specialized Extortion Economics
Ransomware attacks targeting servers represent a particularly destructive breach category with unique financial considerations.
A. The Ransom Dilemma: To Pay or Not to Pay?
Organizations face an impossible decision when servers are encrypted:
-
Ransom Amounts: Typically ranging from $50,000 to millions in cryptocurrency
-
Payment Logistics: Navigating cryptocurrency acquisition and transfer to anonymous wallets
-
Legal Considerations: Potential regulatory prohibition against paying certain threat actors
-
No Guarantee: Paying provides no assurance of data recovery or non-recurrence
B. Ransomware-Specific Costs:
Beyond the ransom itself, organizations face additional expenses:
-
Decryption Tools: Specialized software to attempt data recovery without paying
-
Negotiation Services: Professional negotiators to lower ransom demands
-
Extended Downtime: Systems remain offline throughout the response process
-
Public Relations Crisis Management: Addressing the high-profile nature of ransomware incidents
F. Proactive Financial Protection: Cost Mitigation Strategies
Organizations can significantly reduce potential breach costs through strategic investments in prevention and preparedness.
A. Comprehensive Security Controls Implementation:
A layered defense strategy provides the most effective cost avoidance:
A. Endpoint Detection and Response (EDR): Advanced threat hunting on all servers
B. Network Segmentation: Isolating critical servers from general network access
C. Multi-Factor Authentication (MFA): Required for all administrative server access
D. Privileged Access Management (PAM): Controlling and monitoring administrative credentials
E. Security Information and Event Management (SIEM): Centralized log analysis and threat detection
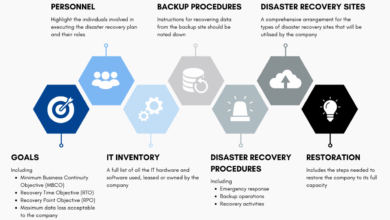
B. Incident Response Planning and Testing:
Preparation dramatically reduces response costs and time:
-
Documented Response Plan: Clear procedures for first 24-48 hours post-breach
-
Tabletop Exercises: Regular simulation of breach scenarios with key stakeholders
-
Retained Experts: Pre-negotiated contracts with forensic and legal specialists
-
Cyber Insurance: Appropriate coverage limits and understanding of policy requirements
C. Data Protection and Backup Strategies:
Proper data management limits breach impact:
-
Encryption: Both at rest and in transit for all sensitive data
-
Regular Backups: Automated, tested, and isolated from production networks
-
Data Classification: Identifying and specially protecting critical information assets
-
Data Retention Policies: Minimizing stored data to reduce breach exposure
D. Security Awareness and Training:
Human factors remain a primary breach vector:
-
Phishing Simulation: Regular testing and training for all employees
-
Administrative Training: Specialized security education for IT staff
-
Social Engineering Defense: Recognizing and reporting sophisticated manipulation attempts
-
Password Hygiene: Implementing and enforcing strong password policies
G. The Cyber Insurance Consideration: Transferring Financial Risk
Cyber insurance has become an essential component of breach cost management, but with important limitations.
A. What Cyber Insurance Typically Covers:
-
Incident Response Costs: Forensics, legal guidance, and public relations
-
Business Interruption: Lost income during recovery period
-
Regulatory Defense: Legal costs associated with regulatory actions
-
Notification Expenses: Customer communication and credit monitoring
-
Ransom Payments: Though increasingly limited by policy exclusions
B. Policy Limitations and Exclusions:
-
Sub-Limits: Caps on specific coverage categories like business interruption
-
Waiting Periods: Time before business interruption coverage activates
-
Security Requirements: Mandated controls that must be in place for coverage
-
Act of War Exclusions: Potential denial for state-sponsored attacks
C. The Insurance Application Process:
-
Security Assessments: Detailed questionnaires about current security posture
-
Third-Party Audits: Independent verification of security controls
-
Remediation Requirements: Necessary improvements before policy issuance
-
Premium Calculations: Based on industry, revenue, and security maturity
Conclusion: The Business Case for Proactive Server Security
The financial impact of a server security breach extends far beyond simple remediation costs, creating a multi-year financial burden that can threaten organizational viability. The most successful organizations recognize that server security is not an IT expense but a strategic business investment. By understanding the complete financial picture—from immediate response costs to long-term reputational damage—business leaders can make informed decisions about security investments and risk acceptance.
The mathematics of prevention consistently proves more favorable than the economics of response. A $500,000 investment in comprehensive server protection looks remarkably prudent when compared to a $5 million breach recovery. In today’s threat landscape, robust server security represents one of the soundest financial decisions an organization can make, protecting not just data but the very business continuity and market position that define long-term success. The question is no longer if organizations should invest in server security, but whether they can afford not to.